Among the key tasks of Digital Forensics and Incident Response (DFIR) specialists is gathering data on both ongoing and resolved incidents and threats. Threat intelligence services, such as ANY.RUN’s TI Lookup, help them reach this goal in the most efficient way.
By implementing threat intelligence tools DFIR teams can learn everything they need to know about threats and gather data required to solve incidents and prevent similar attacks in the future.
DFIR – TI Lookup – Threat Intelligence Tool For Businesses
TI Lookup by ANY.RUN provides a searchable database that encompasses information on threats gathered by 500,000 security professionals worldwide, including Security Operations Center teams from 15,000 companies.
Cybersecurity specialists use ANY.RUN’s Interactive Sandbox for malware analysis, and then data on the threats, including IOCs, IOAs, IOBs, and TTPs, enriches TI Lookup. You can browse it with 40 types of indicators and subscribe for updates on evolving threats.
It provides your team with an efficient tool to:
- Accelerate threat investigation with its flexible search engine and 2-second response time.
- Enhance threat hunting, monitoring, and triage.
- Increase DFIR team members’ expertise by giving access to a large-scale database of fresh threat samples.
- Detect, identify, and react to threats quickly.
Here are three of TI Lookup’s possible use cases.
Link Indicators to Threats
TI Lookup can browse threat samples and their context with dozens of search parameters, including IPs, URLs, domains, hashes, and other events. However, knowing just one of the basic indicators is enough for threat investigation.
For instance, if the only thing you know about a potential threat is an IP address associated with it, start by browsing it:
And in mere seconds you’ll see that this IP address is categorized as malicious and tagged as an example of Quasar malware family.
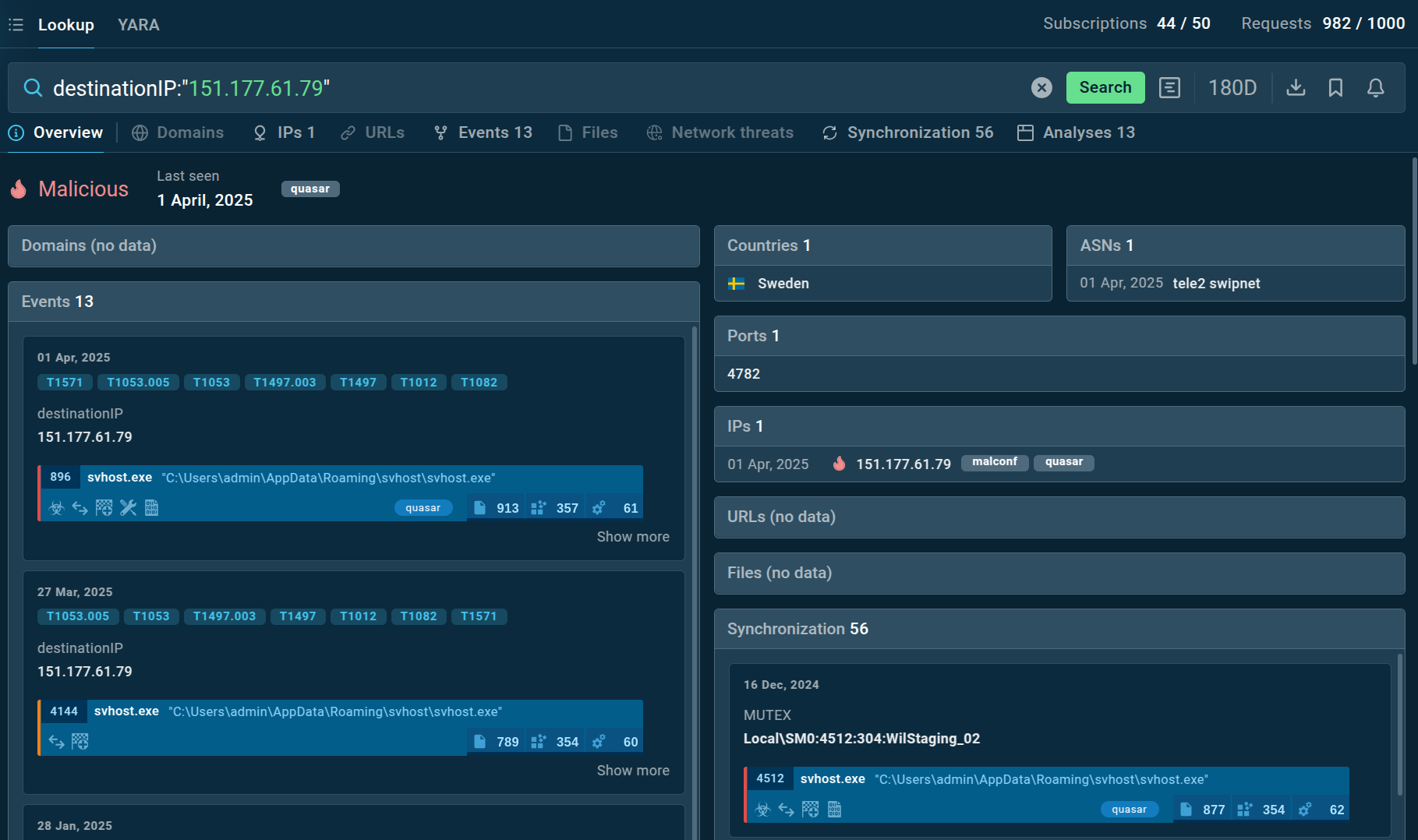 IP address from our request flagged as malicious in TI Lookup
IP address from our request flagged as malicious in TI Lookup
You can also see additional info, such as when it was last detected, which country it originated from, and the number of events associated with it – 13 at the time of writing. Read on to find out how to explore them further to get more useful threat intelligence data.
Try TI Lookup for you company
Learn about Malware’s Behavior
To explore the threat in an in-depth way, as well as to collect more indicators and TTPs that can be used for new TI Lookup queries, use ANY.RUN’s Interactive Sandbox. In its framework, you can see malicious samples unfold in the safe environment of a virtual machine.
Let’s go back to the example from the section above. We started to explore a malicious IP address in TI Lookup and found 13 samples associated with it. Clicking one of them will take us to ANY.RUN’s Interactive Sandbox, where we can observe the threat and conduct an in-depth malware analysis. Interact with the sample just like in a real system and monitor its behavior in detail via the process tree.
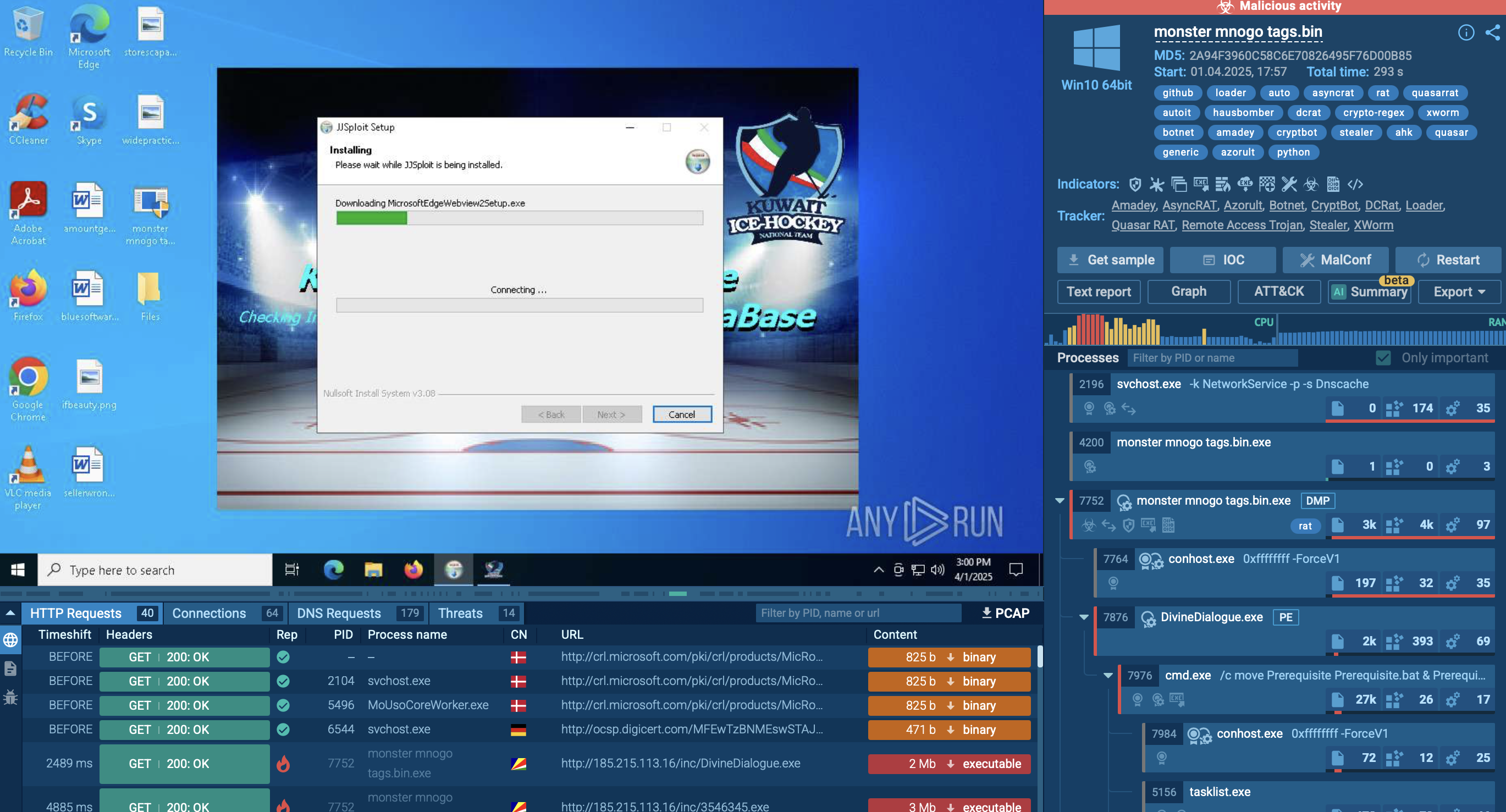 Malware sample analysis in ANY.RUN’s Sandbox
Malware sample analysis in ANY.RUN’s Sandbox
Track Evolving Threats
When it comes to threat intelligence, it’s important to always stay informed. This means tracking both emerging and evolving threats. To make this process easier in TI Lookup, use the Search Updates feature.
It allows you to subscribe to specific queries containing one or several indicators and receive updates on activities that matter to your organization. With Search Updates, it’s easy to monitor threats as they evolve.
Specify your request by listing any of the 40 available parameters. For instance, in case you’d like to check for updates on email-distributed stealers in Colombia, you can use this query: submissionCountry:”co” AND threatName:”stealer” AND filePath:”.eml” OR filePath:”.msg”
Upon entering it, you’ll receive a list of all events and sandbox reports that fit the description.
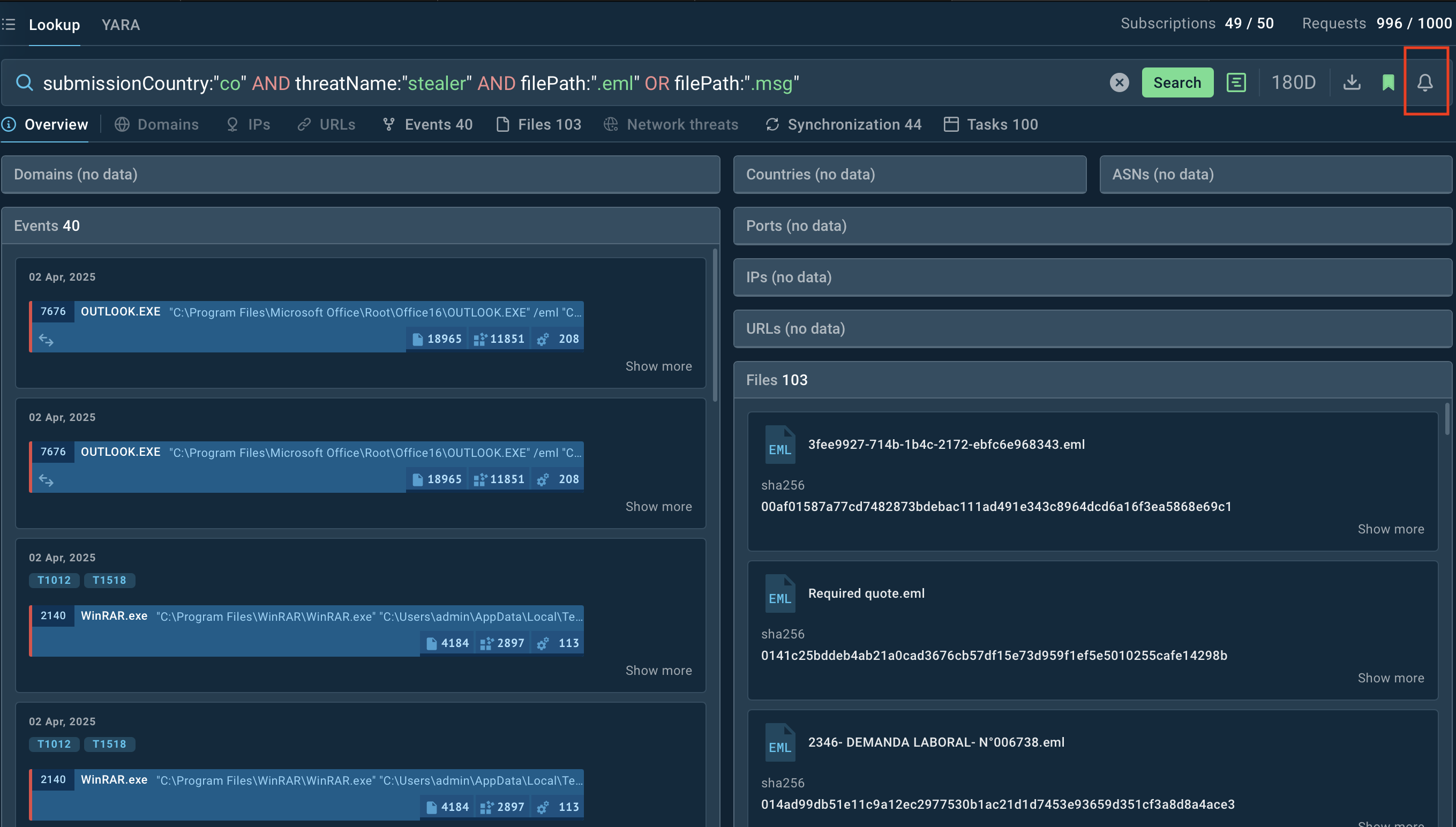 Results of the query mentioned above in TI Lookup
Results of the query mentioned above in TI Lookup
To keep track of them, subscribe to the query by clicking the bell symbol in the top right corner and receive notifications about new related samples in your dashboard (highlighted in green).
For further analysis, go to the sandbox by clicking on the corresponding task.
Conclusion
As you can see, ANY.RUN’s product TI Lookup can provide a powerful tool helping DFIR specialists solve incidents in a number of ways. Get access to the most up-to-date information on cyber threats with 50 trial requests provided by TI Lookup and make most of threat intelligence to ensure the security of your company.
Related News:
Artificial Intelligence (AI) Redefining Thailand’s Financial Landscape
The opinions or information expressed in this press release are solely those of the authors and do not necessarily reflect the views of the Chiang Rai Times. For more information on our sponsored content policy Click Here














